Break Out: The Escape Room Game
Description
The client's Cybersecurity Awareness & Training team was looking for a partner to help them design, develop, host, and deliver a fully remote cybersecurity escape room game.
The Solution
I created a comprehensive, end-to-end solution including Analysis > Design/ Development > Marketing > Sustainment. I, along with the team, designed and developed a 60-minute, hosted game, based on the industry-standard NIST Framework for Cybersecurity, which ensured effective learning impact and comprehensive content coverage. The escape room game format maximized user engagement through captivating storylines, interactivities, graphics, and collaboration.
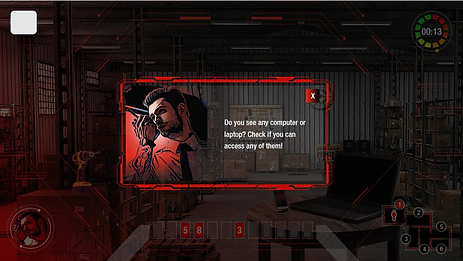
Break out was a 180° escape room combining 3D and 2D elements, where learners had the facility to explore the room and manipulate objects.
Story elements
In the game design, I address the questions: “who, what, when, where, why, and how” to weave together the narrative.
WHO
The players are the “heroes” in the story. The “victim” has been trapped by a “villain” who is planning to crash the organization’s network.
WHAT
The players need to solve 12 puzzles scattered around 6 rooms. The victim gives them clues about what objects to look for and the learners need to inspect and solve them.
WHEN
The game has a 60-minute time limit after which the players lose and need to restart.
WHERE
The game is set in a storage facility belonging to Tech One, an engineering firm. It has several rooms and the victim is trapped in one of them. The clues are distributed across 6 rooms.
WHY
The players have to find the location of the hacker before time runs out and the organization’s global network is shut down.
HOW
The players are given information related to cybersecurity (video/ audio clips, posters, hints, feedback) to facilitate learning.
Storyline
Zack Hayley's in trouble. He's locked inside a room at his company, Tech One’s, storage facility. The unfortunate result of having uncovered a hacker’s plot to crash Tech One's global network.
As the hacker speeds towards Tech One’s main control room, Zack finds an old radio in the room.
He sends out a mayday signal but...
Will anyone hear him in time?
Will he manage to Break Out?














Additional Features
The solution included additional features such as:
-
Multiplayer mode: In this mode, groups of learners played the game at the same time as part of the same team. Any object manipulation done by one player was seen by other players. Similarly, any screens, videos, etc. were visible to all players in the room.
-
Text chat: Players could exchange ideas and share learnings via text chat. The chat window could be turned on/off by players.
-
Leaderboard: The scores were calculated based on the number of puzzles solved and the time taken to solve them.
-
Badges: Players earned badges for each correct solution to reward their achievements and keep engagement levels high.
-
Hosting: Infrastructure for solution delivery and learner tracking were also provided.
Learning Model - LEAP Framework

Content Design
The solution was aligned with the NIST framework, an industry-standard approach that guides organizations to successfully implement cybersecurity initiatives.
1. Identify
Develop an organizational understanding to manage cybersecurity risks to systems, assets, data, and capabilities. E.g., maintaining a payment gateway.
2. Protect
Develop and implement the appropriate safeguards to ensure delivery of services. E.g., ensure firewalls are installed and running.
3. Detect
Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event. E.g., leakage of confidential customer information.
4. Respond
Develop and implement the appropriate activities to take action regarding a detected cybersecurity event. E.g., ensure that response plans are in place and regularly updated.
5. Recover
Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event. E.g., communicate with stakeholders and manage company reputation.
After completing the game and after having internalized the cybersecurity topics and the best practices employed by Cummins, to retain the efficacy of learning and to keep the subject relevant at all times, I conducted a set of activities at periodic intervals of a month as part of a Learning Sustainment Plan. These activities were seasonal such as themes around Christmas, or linked with organizational initiatives.
Learning Sustainment
